In context: CovertNetwork-1658 is a stark reminder of the continuing cat-and-mouse recreation between cybersecurity professionals and risk actors. Utilizing compromised units as a part of a botnet additionally underscores the significance of securing IoT units and commonly updating firmware on routers and different community gear.
Microsoft has uncovered a fancy community of compromised units that Chinese language hackers are utilizing to launch extremely evasive password spray assaults towards Microsoft Azure clients. This community, dubbed CovertNetwork-1658 by Microsoft, has been actively stealing credentials from a number of Microsoft clients since August 2023.
The assaults use a botnet of 1000’s of small workplace and residential workplace (SOHO) routers, cameras, and different Web-connected units. At its peak, there have been greater than 16,000 units within the botnet, most of which had been TP-Hyperlink routers.
CovertNetwork-1658, often known as xlogin and Quad7 (7777), is believed to be established and maintained by a risk actor positioned in China. The community’s identify stems from Microsoft’s classification system, the place “CovertNetwork” refers to a set of egress IPs consisting of compromised or leased units that could be utilized by a number of risk actors.
The hackers exploit a vulnerability within the routers to realize distant code execution functionality, though the precise exploit technique remains to be underneath investigation. As soon as entry is achieved, the risk actors take a number of steps to arrange the router for password spray operations. These steps embody downloading Telnet and xlogin backdoor binaries from a distant File Switch Protocol (FTP) server, beginning an access-controlled command shell on TCP port 7777, and organising a SOCKS5 server on TCP port 11288.
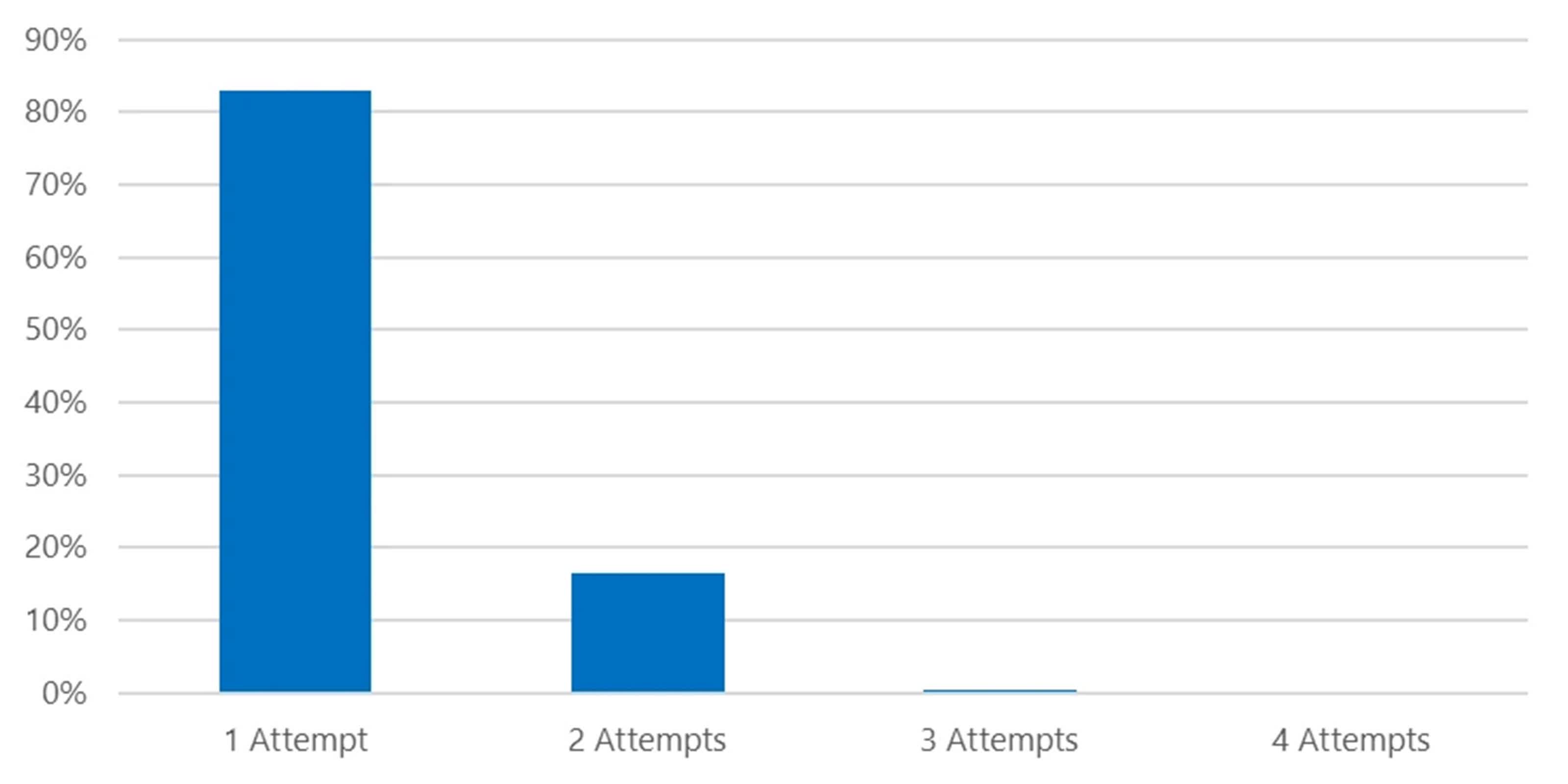
CovertNetwork-1658 is extremely evasive, making it notably harmful. The password spray assaults are carried out by means of this proxy community, guaranteeing that the makes an attempt originate from the compromised units. In about 80 % of circumstances, CovertNetwork-1658 makes just one sign-in try per account every day, making it tough to detect utilizing conventional safety measures.
The community additionally makes use of compromised SOHO IP addresses, a rotating set of IP addresses, and the low-volume password spray course of. On common, Microsoft has noticed about 8,000 compromised units actively engaged within the CovertNetwork-1658 community at any given time, with roughly 20 % of those units performing password spraying.
Microsoft has linked the supply of those password spray assaults to a number of Chinese language risk actors. Particularly, a gaggle referred to as Storm-0940 has been noticed utilizing credentials obtained from CovertNetwork-1658. The connection between CovertNetwork-1658 and Storm-0940 seems to be shut, with Microsoft having noticed Storm-0940 utilizing compromised credentials obtained from CovertNetwork-1658 on the identical day.
As soon as Storm-0940 positive aspects entry to a sufferer’s setting, it makes use of varied techniques to increase its attain. These embody scanning and credential dumping instruments for lateral motion inside the community, trying to entry community units and set up proxy instruments and distant entry trojans (RATs) for persistence, and trying to exfiltrate information.
The dimensions of this operation is especially regarding, as any risk actor utilizing the CovertNetwork-1658 infrastructure can conduct large password-spraying campaigns. This, mixed with the fast turnover of compromised credentials between CovertNetwork-1658 and Chinese language risk actors, means accounts may be compromised shortly throughout a number of sectors and geographic areas.
Whereas latest stories from safety distributors like Sekoia and Workforce Cymru have led to a decline within the utilization of CovertNetwork-1658’s unique infrastructure, Microsoft believes that the community remains to be operational and that risk actors are doubtless buying new infrastructure with modified fingerprints to evade detection.
Microsoft has straight notified focused or compromised clients. Whereas Redmond did not present particular recommendation on how customers of TP-Hyperlink routers and different affected units can stop or detect infections, some consultants recommend that periodically rebooting these units could assist disinfect them quickly.




/cdn.vox-cdn.com/uploads/chorus_asset/file/23324425/VRG_ILLO_5090_The_best_Fitbit_for_your_fitness_and_health.jpg)